Cameras are down. Not the endpoint installing their firmwares. Open socket here. Could analyze some outdated firmwares.
Introduction #
This challenge was created for the Computer Science Games 2024, a university competition. The theme was a battle against ChlorophyllAI, an evil artificial intelligence wanting to take over the world and destroy humanity. This explains the somewhat strange challenge descriptions.
I designed it for multiple reasons:
- Raising awareness about IoT cybersecurity
- Deepening my understanding of Yocto and kas
- Giving back to the community
If you are interested in IoT cybersecurity as well, feel free to use all of this material to host a friendly competition at your work or learn with your friends!
The challenges themselves were inspired by both the OWASP IoT Top 10 and personal experiences.
Setup #
The challenge and all of its components are fully open-source. It was designed so that anyone can build it, install it, and learn from it.
The firmware can be built from the files in this repository. It is compatible with the Raspberry Pi 3 and 4. Pre-built firmmare binaries are also available at TODO.
If you want the full CSGames experience, you can also set up the CTFd which contains the
TODO: changer le readme dans le repo meta-csgames
First steps #
The first step is to download the firmware (the one called for_players). Then, we need to figure out what to do with it. The file utility can give us a starting point.
firmware.rpi-sdimg: DOS/MBR boot sector; partition 1 : ID=0xc, active, start-CHS (0x40,0,1), end-CHS (0x33f,3,32), startsector 8192, 98304 sectors; partition 2 : ID=0x83, start-CHS (0x340,0,1), end-CHS (0x3ff,3,32), startsector 106496, 1933312 sectors
The file is a MBR disk with 2 partitions, which makes sense knowing that the image is normally flashed on an SD card. We can get more details using fdisk -l.
Disk firmware.rpi-sdimg: 996 MiB, 1044381696 bytes, 2039808 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0xdf235d16
Device Boot Start End Sectors Size Id Type
firmware.rpi-sdimg1 * 8192 106495 98304 48M c W95 FAT32 (LBA)
firmware.rpi-sdimg2 106496 2039807 1933312 944M 83 Linux
The first partition is the FAT32 boot partition and the second seems to be a Linux filesystem. Since we are looking for vulnerable applications, the latter is much more interesting.
Accessing the filesystem #
To access the filesystem inside the image, we have 2 main options:
- Extract it on our own filesystem
- Mount the partition and access it directly
Both options are equally viable, so let’s have a look.
Extracting the filesystem #
The most well known tool for extracting files from binary blobs is binwalk. However, it’s so sensitive that it takes quite some time and submerges us with pages of output. The newer unblob is much faster and quieter.
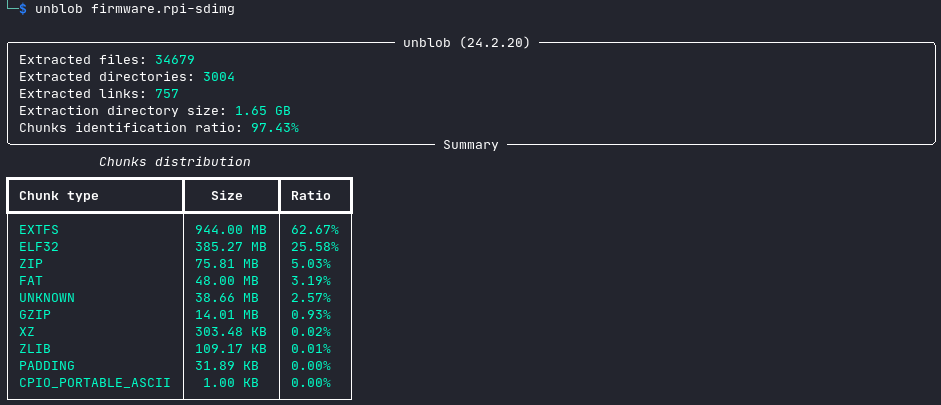
The filesystem is then available in firmware.rpi-sdimg_extract/54525952-1044381696.extfs_extract/.
Mounting the partition #
The mount command requires the offset of the partition in the image. The output of fdisk from earlier indicates a start sector of 106496. Since sectors are 512 bytes long, the offset of the partition in bytes is 106496 * 512 = 54525952.
Here is the resulting command:
sudo mount -o offset=54525952 ./firmware.rpi-sdimg /mnt
The filesystem is then available in /mnt.
First flag #
Whichever method you used, you can find your first flag in the root of the filesystem, congratz!
Reconaissance #
We want to use the firmware to gain access to the real system. For that, we need either secret information, such as:
- Credentials
- Passwords
- Keys
- Tokens
- Configuration files
Or we need to find potentially vulnerable code, like:
- Custom applications
- System services
- Cron jobs
- Scripts
Secrets #
Let’s start with the secrets. A few places come to mind for secret information on a Linux system.
/root: empty/etc/shadow: there is a hash which we can try to crack later
caladium:$1$4ddHJV4I$MonYyEt8pCEehm/yyD9YB0:15069:0:99999:7:::
/etc: contains too many files to check them all now/home: only has one directory/home/caladium: appart from the normal/var/www:
Let’s not forget to chmod 600
Code #
Now
Plan #
- Introduction
- Why this challenge
- Meant as a workshop that anyone can do to practice yourself
- OWASP IoT Top 10??
- 8 flags in total
- Why this challenge
- Setup
- Build it yourself
- Yocto
- Flash on your raspberry pi
- Pre-build images
- DHCP or static IP
- CTFd optional
- TODO: Changer le username et mot de passe!
- Build it yourself
- Methodology
- Reverse the firmware to gain access to the real system
- What can we do with the firmware provided?
- What is the file?
- Partitions
- Extract it
- Mount it
- First flag!
- Firmware investigation
- What are we looking for?
- Secrets
- Code
- Where do we look?
- What can we find?
- What are we looking for?
- Finding services
- nmap
- netstat
- systemd
- FTP